Morphisec Moving Target
Next generation, automated cybersecurity for stopping ransomware, supply chain attacks, zero-days, fileless and other undetectable attacks in-memory at runtime. Ideal for augmenting NGAV, EDR and XDR with no additional staff needed and no performance impact on endpoints or servers.
Ready to Stop 30% of Attacks that
Bypass EDR/XDR & NGAV
Why is Morphisec Needed?
Next generation antivirus (NGAV), endpoint protection platforms (EPP), and endpoint detection and response (EDR and XDR) solutions stop known attacks with recognised signatures and behavioral patterns, but they often do not detect or prevent the more disruptive advanced attacks organisations are experiencing today – the undetectable attacks such as zero-days, malware variants or supply chain attacks that lead to ransomware. A new technology recognised by Gartner is proven to stop advanced threats on both Windows and Linux systems, making prevention-first security a reality.
- Data Encryption & Destruction Protection
- System Recovery Tamper Protection
- Credential Theft Protection
- Runtime Memory Protection with Automated Moving Target Defense (AMTD)
- NGAV, EPP, & EDR/XDR
Proactively Prevent Evasive Threats that Bypass
Today's AV, EDR and EPP solutions
Morphisec is the only solution designed to protect critical applications from the advanced threats that evade detection-based solutions. All without the need for prior knowledge.
Preemptive Cyber Security
Morphisec proactively prevents evasive threats that bypass today's AV, EDR and EPP solutions
Save Time & Resources
No investigation, threat hunting or pursuit of thousands of false positives
Zero trust at Runtime
Evasive threats can't gain persistence in corporate systems
Key Features of Morphisec (AMTD)
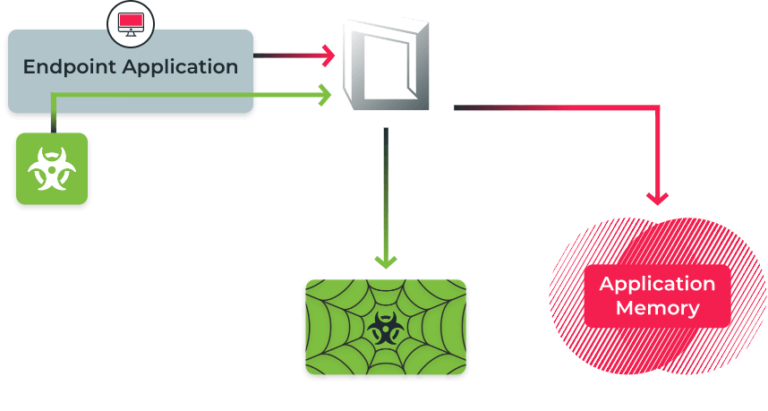
Unlike other endpoint protection solutions which must first detect an attack in order to stop it, Morphisec prevents advanced attacks from executing by dismantling their delivery mechanisms and kill chain. Morphisec uses patented Moving Target Defense technology to morph the memory space layout so adversaries cannot find an entry point, or the resources required, to execute an attack. This real-time, one-way randomisation prevents highly sophisticated attacks, including the most advanced exploits and fileless malware.
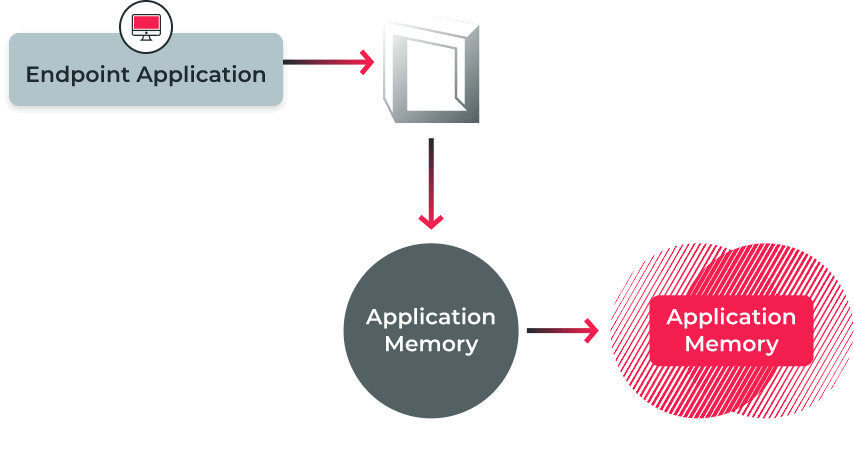
Morph & Conceal
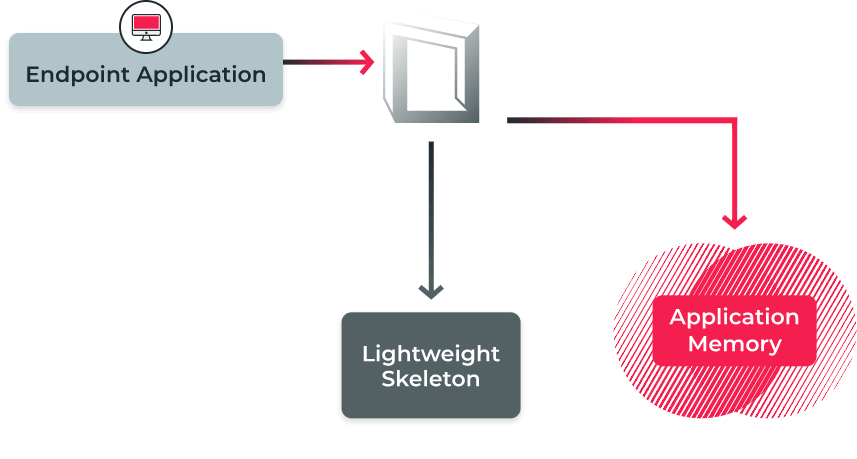
Protect & Deceive