Astrix Security on 3rd Party Integrations
Are you ready to protect your SaaS-to-SaaS supply chain from hidden threats? Learn how Astrix Security can deliver comprehensive visibility, automated risk assessment, and proactive threat mitigation across your entire SaaS environment.
Astrix Security
The proliferation of SaaS apps and third-party integrations has fundamentally changed the way businesses operate. While these tools boost productivity, they also introduce hidden vulnerabilities in your SaaS-to-SaaS supply chain. At ITR, we understand that modern enterprises need robust solutions to secure these external connections. That’s why we’re proud to be a value-added reseller of Astrix Security, a platform purpose-built to safeguard all your critical SaaS integrations and prevent costly supply chain attacks.
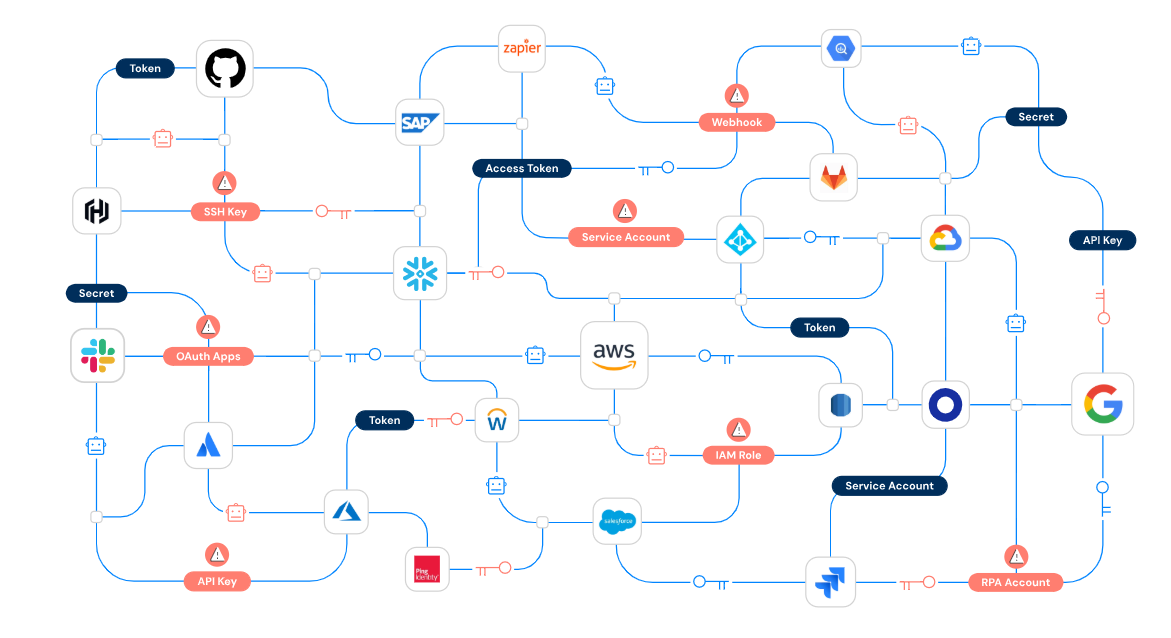
How Does Astrix Security Work?
Comprehensive Visibility
Astrix Security scans and catalogues every external SaaS integration in your environment, revealing potentially overlooked, or “shadow,” connections.
Token-Based Access & Risk Assessment
The platform identifies which services have privileged access to your sensitive data, using token-based analysis to spot risky permissions and configurations.
Continuous Monitoring & Alerting
With automated scanning, Astrix Security detects changes in real-time—whether it’s an app requesting additional privileges or new connections being formed.
Adaptive Threat Mitigation
Astrix not only flags vulnerabilities but also suggests immediate actions—such as revoking token access or applying least privilege principles—to reduce your risk profile.
Whats pains does it fix?
Many enterprises remain unaware of how third-party SaaS apps can introduce backdoors for attackers. Astrix Security uncovers and manages these hidden threats.

Hidden Integration Vulnerabilities

Token Privilege Bloat

Manual Processes & Fragmented Tools

Regulatory Compliance & Audits
What Sets Astrix Security Apart?
End-to-End SaaS
Security Instead of a patchwork solution, Astrix Security delivers a single pane of glass to manage every aspect of your third-party integrations.
Continuous, Automated Protection
Through automated scanning and proactive alerting, Astrix eliminates guesswork, reducing the time needed for manual checks and intervention.
Seamless Integration
Astrix Security easily integrates with your existing tech stack—supporting a wide range of SaaS platforms—ensuring minimal downtime and a quick path to value.
Tailored Recommendations
Rather than simply listing vulnerabilities, Astrix provides actionable insights, offering clear remediation steps to fix high-risk exposures.
Are you ready to protect your SaaS-to-SaaS supply chain from hidden threats? Contact ITR today to learn how Astrix Security can deliver comprehensive visibility, automated risk assessment, and proactive threat mitigation across your entire SaaS environment. We’re here to help you implement, configure, and maintain Astrix so you can focus on driving innovation—without compromising on security.
Get in touch with ITR now and safeguard your business from the next wave of supply chain attacks.

